How would you configure your distsearch conf to allow you to run the search below?
sourcetype=access_combined status=200 action=purchase
splunk_setver_group=HOUSTON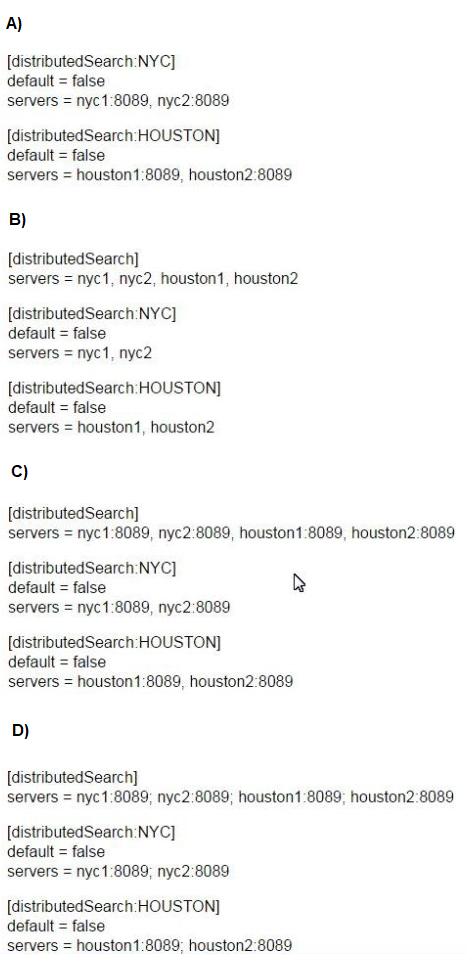
A. Option A
B. Option B
C. Option C
D. Option C
What is the correct curl to send multiple events through HTTP Event Collector?
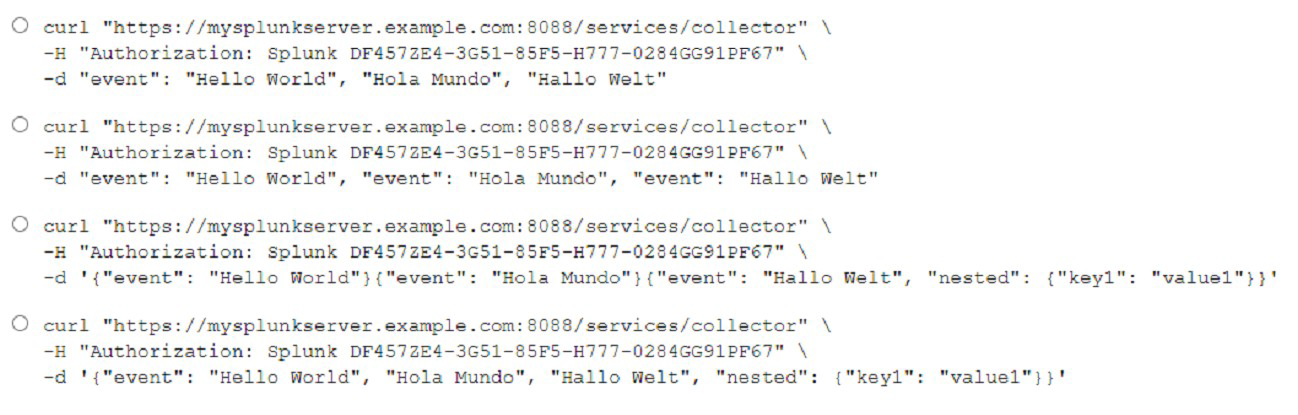
A. Option A
B. Option B
C. Option C
D. Option D
Explanation: curl “https://mysplunkserver.example.com:8088/services/collector” \ -H
“Authorization: Splunk DF4S7ZE4-3GS1-8SFS-E777-0284GG91PF67” \ -d ‘{“event”: “Hello
World”}, {“event”: “Hola Mundo”}, {“event”: “Hallo Welt”}’. This is the correct curl command
to send multiple events through HTTP Event Collector (HEC), which is a token-based API
that allows you to send data to Splunk Enterprise from any application that can make an
HTTP request. The command has the following components:
The URL of the HEC endpoint, which consists of the protocol (https), the hostname
or IP address of the Splunk server (mysplunkserver.example.com), the port
number (8088), and the service name (services/collector).
The header that contains the authorization token, which is a unique identifier that
grants access to the HEC endpoint. The token is prefixed with Splunk and
enclosed in quotation marks. The token value (DF4S7ZE4-3GS1-8SFS-E777-
0284GG91PF67) is an example and should be replaced with your own token
value.
The data payload that contains the events to be sent, which are JSON objects
enclosed in curly braces and separated by commas. Each event object has a
mandatory field called event, which contains the raw data to be indexed. The event
value can be a string, a number, a boolean, an array, or another JSON object. In
this case, the event values are strings that say hello in different languages.
A new forwarder has been installed with a manually createddeploymentclient.conf.
What is the next step to enable the communication between the forwarder and the
deployment server?
A. Restart Splunk on the deployment server.
B. Enable the deployment client in Splunk Web under Forwarder Management.
C. Restart Splunk on the deployment client.
D. Wait for up to the time set in thephoneHomeIntervalInSecssetting.
Explanation: The next step to enable the communication between the forwarder and the deployment server after installing a new forwarder with a manually created deploymentclient.conf is to restart Splunk on the deployment client. The deploymentclient.conf file contains the settings for the deployment client, which is a Splunk instance that receives updates from the deployment server. The file must include the targetUri attribute, which specifies the hostname and management port of the deployment server. To apply the changes in the deploymentclient.conf file, Splunk must be restarted on the deployment client. Therefore, option C is the correct answer.
In this source definition the MAX_TIMESTAMP_LOOKHEAD is missing. Which value would fit best?
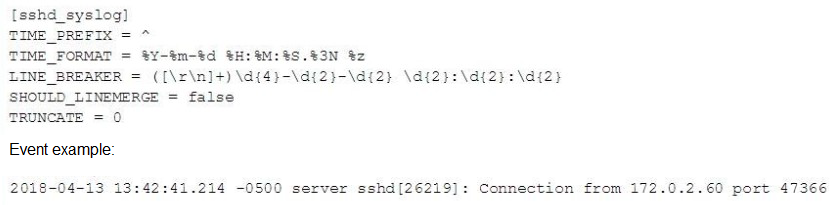
A. MAX_TIMESTAMP_L0CKAHEAD = 5
B. MAX_TIMESTAMP_LOOKAHEAD - 10
C. MAX_TIMESTAMF_LOOKHEAD = 20
D. MAX TIMESTAMP LOOKAHEAD - 30
"Specify how far (how many characters) into an event Splunk software should look for a timestamp." since TIME_PREFIX = ^ and timestamp is from 0-29 position, so D=30 will pick up the WHOLE timestamp correctly.
What is the correct example to redact a plain-text password from raw events?
A. in props.conf:
[identity]
REGEX-redact_pw = s/password=([^,|/s]+)/ ####REACTED####/g
B. in props.conf:
[identity]
SEDCMD-redact_pw = s/password=([^,|/s]+)/ ####REACTED####/g
C. in transforms.conf:
[identity]
SEDCMD-redact_pw = s/password=([^,|/s]+)/ ####REACTED####/g
D. in transforms.conf:
[identity]
REGEX-redact_pw = s/password=([^,|/s]+)/ ####REACTED####/g
Explanation: The correct answer is B. in props.conf:
[identity]
SEDCMD-redact_pw = s/password=([^,|/s]+)/ ####REACTED####/g
According to the Splunk documentation1, to redact sensitive data from raw events, you
need to use the SEDCMD attribute in the props.conf file. The SEDCMD attribute applies a
sed expression to the raw data before indexing. The sed expression can use the s
command to replace a pattern with a substitution string. For example, the following sed
expression replaces any occurrence of password= followed by any characters until a
comma, whitespace, or slash with ####REACTED####:
s/password=([^,|/s]+)/ ####REACTED####/g
The g flag at the end means that the replacement is applied globally, not just to the first
match.
Option A is incorrect because it uses the REGEX attribute instead of the SEDCMD
attribute. The REGEX attribute is used to extract fields from events, not to modify them.
Option C is incorrect because it uses the transforms.conf file instead of the props.conf file.
The transforms.conf file is used to define transformations that can be applied to fields or
events, such as lookups, evaluations, or replacements. However, these transformations are
applied after indexing, not before.
Option D is incorrect because it uses both the wrong attribute and the wrong file. There is
no REGEX-redact_pw attribute in the transforms.conf file.
References:1:Redact data from events - Splunk Documentation
Which of the following is the use case for the deployment server feature of Splunk?
A. Managing distributed workloads in a Splunk environment
B. Automating upgrades of Splunk forwarder installations on endpoints
C. Orchestrating the operations and scale of a containerized Splunk deployment
D. Updating configuration and distributing apps to processing components, primarily forwarders.
"The deployment server is the tool for distributing configurations, apps, and content updates to groups of Splunk Enterprise instances."
| Page 2 out of 31 Pages |
| Previous |