When adding a directory monitor and specifying a sourcetype explicitly, it applies to all files in the directory and subdirectories. If automatic sourcetyping is used, a user can selectively override it in which file on the forwarder?
A. transforms.conf
B. props.conf
C. inputs.conf
D. outputs.cont
Explanation: When a directory monitor is set up with automatic sourcetyping, a user can selectively override the sourcetype assignment by configuring the props.conf file on the forwarder. The props.conf file allows you to define how data should be parsed and processed, including assigning or overriding sourcetypes for specific data inputs.
When using Splunk Universal Forwarders, which of the following is true?
A. No more than six Universal Forwarders may connect directly to Splunk Cloud.
B. Any number of Universal Forwarders may connect directly to Splunk Cloud.
C. Universal Forwarders must send data to an Intermediate Forwarder.
D. There must be one Intermediate Forwarder for every three Universal Forwarders.
Explanation: Universal Forwarders can connect directly to Splunk Cloud, and there is no limit on the number of Universal Forwarders that may connect directly to it. This capability allows organizations to scale their data ingestion easily by deploying as many Universal Forwarders as needed without the requirement for intermediate forwarders unless additional data processing, filtering, or load balancing is required.
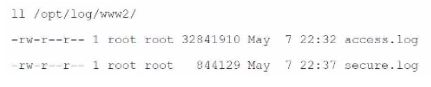
Which monitor statement will retrieve only files that start with "access" in the directory /opt/log/ww2/?
A. [monitor:///opt/lug/.../access]
B. [monitor:///opt/log/www2/access*]
C. [monitor:///opt/log/www2/]
D. [monitor:///opt/log/.../]
Explanation: The correct monitor statement to retrieve only files that start with "access" in the directory /opt/log/www2/ is [monitor:///opt/log/www2/access*]. This configuration specifically targets files that begin with the name "access" and will match any such files within that directory, such as "access.log".
The following Apache access log is being ingested into Splunk via a monitor input:
How does Splunk determine the time zone for this event?
A. The value of the TZ attribute in props. cont for the a :ces3_ccwbined sourcetype.
B. The value of the TZ attribute in props, conf for the my.webserver.example host.
C. The time zone of the Heavy/Intermediate Forwarder with the monitor input.
D. The time zone indicator in the raw event data.
Explanation: In Splunk, when ingesting logs such as an Apache access log, the time zone
for each event is typically determined by the time zone indicator present in the raw event
data itself. In the log snippet you provided, the time zone is indicated by -0400, which
specifies that the event's timestamp is 4 hours behind UTC (Coordinated Universal Time).
Splunk uses this information directly from the event to properly parse the timestamp and
apply the correct time zone. This ensures that the event's time is accurately reflected
regardless of the time zone in which the Splunk instance or forwarder is located.
Splunk Cloud Reference: For further details, you can review Splunk documentation on
timestamp recognition and time zone handling, especially in relation to log files and data
ingestion configurations.
Which of the following is a correct statement about Universal Forwarders?
A. The Universal Forwarder must be able to contact the license master.
B. A Universal Forwarder must connect to Splunk Cloud via a Heavy Forwarder.
C. A Universal Forwarder can be an Intermediate Forwarder.
D. The default output bandwidth is 500KBps.
Explanation: A Universal Forwarder (UF) can indeed be configured as an Intermediate
Forwarder. This means that the UF can receive data from other forwarders and then
forward that data on to indexers or Splunk Cloud, effectively acting as a relay point in the
data forwarding chain.
Option A is incorrect because a Universal Forwarder does not need to contact the
license master; only indexers and search heads require this.
Option B is incorrect as Universal Forwarders can connect directly to Splunk Cloud
or via other forwarders.
Option D is also incorrect because the default output bandwidth limit for a UF is
typically much higher than 500KBps (default is 256KBps per pipeline, but can be
configured).
A customer has worked with their LDAP administrator to configure an LDAP strategy in Splunk. The configuration works, and user Mia can log into Splunk using her LDAP Account. After some time, the Splunk Cloud administrator needs to move Mia from the user role to the power role. How should they accomplish this?
A. Ask the LDAP administrator to move Mia's account to an appropriately mapped LDAP group.
B. Have Mia log into Splunk, then update her own role in user settings.
C. Create a role named Power in Splunk, then map Mia's account to that role.
D. Use the Cloud Monitoring Console app as an administrator to map Mia's account to the power role.
Explanation: In Splunk Cloud, role-based access controls are managed by mapping LDAP groups to Splunk roles. Therefore, any change in roles should be managed by the LDAP administrator, who can adjust Mia’s group to an LDAP group mapped to the power role.
| Page 1 out of 14 Pages |